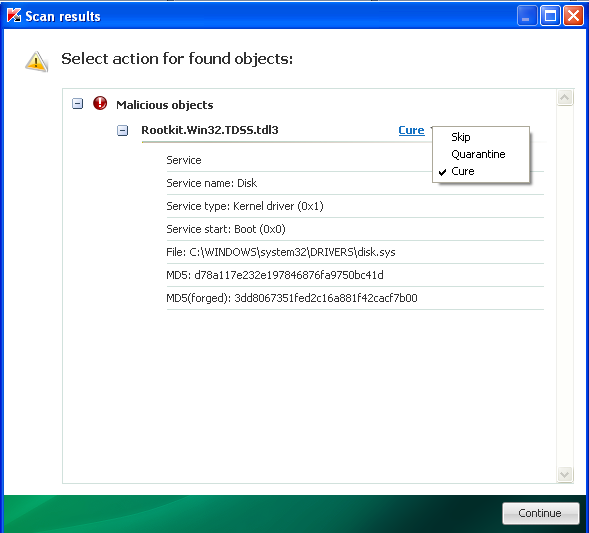
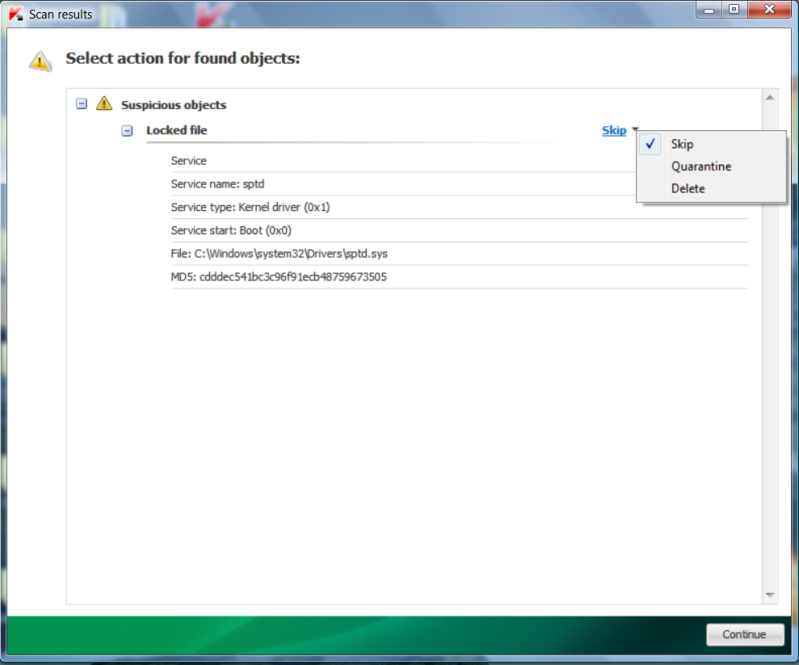
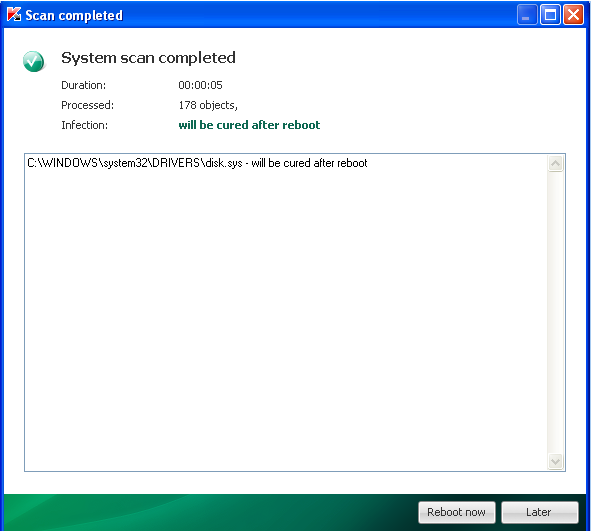
Hello, after running TDSSkiller i feel we have made good progress. i rebooted
without Windows Recovery Environment. I was now able to download SAS! Below are two SAS scan logs 1st quick scan 2nd complete scan.
SUPERAntiSpyware Scan Log
http://www.superantispyware.comGenerated 05/01/2012 at 09:17 PM
Application Version : 5.0.1148
Core Rules Database Version : 8535
Trace Rules Database Version: 6347
Scan type : Quick Scan
Total Scan Time : 00:24:52
Operating System Information
Windows XP Home Edition 32-bit, Service Pack 3 (Build 5.01.2600)
Administrator
Memory items scanned : 529
Memory threats detected : 0
Registry items scanned : 29850
Registry threats detected : 0
File items scanned : 17724
File threats detected : 522
Trojan.Agent/Gen-FakeAntiSpy
C:\DOCUMENTS AND SETTINGS\ALL USERS\APPLICATION DATA\JL6SVP0H5ESLEV.EXE
C:\WINDOWS\Prefetch\JL6SVP0H5ESLEV.EXE-2DDEBA6B.pf
PUP.Whitesmoke
C:\Program Files\WHITESMOKE
Adware.Tracking Cookie
C:\Documents and Settings\Stephen\Cookies\stephen@006.free-counters.co[2].txt [ /006.free-counters.co ]
C:\Documents and Settings\Stephen\Cookies\stephen@112.2o7[2].txt [ /112.2o7 ]
C:\Documents and Settings\Stephen\Cookies\stephen@122.2o7[2].txt [ /122.2o7 ]
C:\Documents and Settings\Stephen\Cookies\stephen@122.2o7[3].txt [ /122.2o7 ]
C:\Documents and Settings\Stephen\Cookies\stephen@192com.112.2o7[1].txt [ /192com.112.2o7 ]
C:\Documents and Settings\Stephen\Cookies\stephen@2012-thecountdown[1].txt [ /2012-thecountdown ]
C:\Documents and Settings\Stephen\Cookies\stephen@247realmedia[2].txt [ /247realmedia ]
C:\Documents and Settings\Stephen\Cookies\stephen@2o7[2].txt [ /2o7 ]
C:\Documents and Settings\Stephen\Cookies\stephen@77tracking[1].txt [ /77tracking ]
C:\Documents and Settings\Stephen\Cookies\stephen@a1.interclick[2].txt [ /a1.interclick ]
C:\Documents and Settings\Stephen\Cookies\stephen@account.live[2].txt [ /account.live ]
C:\Documents and Settings\Stephen\Cookies\stephen@accounts.google[3].txt [ /accounts.google ]
C:\Documents and Settings\Stephen\Cookies\stephen@ad.360yield[1].txt [ /ad.360yield ]
C:\Documents and Settings\Stephen\Cookies\stephen@ad.adperium[1].txt [ /ad.adperium ]
C:\Documents and Settings\Stephen\Cookies\stephen@ad.bodybuilding[2].txt [ /ad.bodybuilding ]
C:\Documents and Settings\Stephen\Cookies\stephen@ad.pitattomatch[1].txt [ /ad.pitattomatch ]
C:\Documents and Settings\Stephen\Cookies\stephen@ad.yieldmanager[1].txt [ /ad.yieldmanager ]
C:\Documents and Settings\Stephen\Cookies\stephen@ad.zanox[2].txt [ /ad.zanox ]
C:\Documents and Settings\Stephen\Cookies\stephen@ad1.emediate[1].txt [ /ad1.emediate ]
C:\Documents and Settings\Stephen\Cookies\stephen@adbrite[1].txt [ /adbrite ]
C:\Documents and Settings\Stephen\Cookies\stephen@adform[1].txt [ /adform ]
C:\Documents and Settings\Stephen\Cookies\stephen@ads.ad4game[2].txt [ /ads.ad4game ]
C:\Documents and Settings\Stephen\Cookies\stephen@ads.adap[2].txt [ /ads.adap ]
C:\Documents and Settings\Stephen\Cookies\stephen@ads.anm.co[2].txt [ /ads.anm.co ]
C:\Documents and Settings\Stephen\Cookies\stephen@ads.aol.co[1].txt [ /ads.aol.co ]
C:\Documents and Settings\Stephen\Cookies\stephen@ads.associatedcontent[1].txt [ /ads.associatedcontent ]
C:\Documents and Settings\Stephen\Cookies\stephen@ads.audience2media[2].txt [ /ads.audience2media ]
C:\Documents and Settings\Stephen\Cookies\stephen@ads.audience2media[3].txt [ /ads.audience2media ]
C:\Documents and Settings\Stephen\Cookies\stephen@ads.bleepingcomputer[2].txt [ /ads.bleepingcomputer ]
C:\Documents and Settings\Stephen\Cookies\stephen@ads.blogtalkradio[2].txt [ /ads.blogtalkradio ]
C:\Documents and Settings\Stephen\Cookies\stephen@ads.blogtalkradio[3].txt [ /ads.blogtalkradio ]
C:\Documents and Settings\Stephen\Cookies\stephen@ads.carocean.co[1].txt [ /ads.carocean.co ]
C:\Documents and Settings\Stephen\Cookies\stephen@ads.ctasnet[2].txt [ /ads.ctasnet ]
C:\Documents and Settings\Stephen\Cookies\stephen@ads.foodbuzz[2].txt [ /ads.foodbuzz ]
C:\Documents and Settings\Stephen\Cookies\stephen@ads.gmodules[2].txt [ /ads.gmodules ]
C:\Documents and Settings\Stephen\Cookies\stephen@ads.monster[1].txt [ /ads.monster ]
C:\Documents and Settings\Stephen\Cookies\stephen@ads.monster[2].txt [ /ads.monster ]
C:\Documents and Settings\Stephen\Cookies\stephen@ads.moviemaker[1].txt [ /ads.moviemaker ]
C:\Documents and Settings\Stephen\Cookies\stephen@ads.nsi-ltd[2].txt [ /ads.nsi-ltd ]
C:\Documents and Settings\Stephen\Cookies\stephen@ads.ogdenpubs[1].txt [ /ads.ogdenpubs ]
C:\Documents and Settings\Stephen\Cookies\stephen@ads.pubmatic[2].txt [ /ads.pubmatic ]
C:\Documents and Settings\Stephen\Cookies\stephen@ads.raasnet[1].txt [ /ads.raasnet ]
C:\Documents and Settings\Stephen\Cookies\stephen@ads.roiserver[2].txt [ /ads.roiserver ]
C:\Documents and Settings\Stephen\Cookies\stephen@ads.simonandschuster[1].txt [ /ads.simonandschuster ]
C:\Documents and Settings\Stephen\Cookies\stephen@ads.telegraph.co[1].txt [ /ads.telegraph.co ]
C:\Documents and Settings\Stephen\Cookies\stephen@ads.torrentreactor[2].txt [ /ads.torrentreactor ]
C:\Documents and Settings\Stephen\Cookies\stephen@ads.uknetguide.co[1].txt [ /ads.uknetguide.co ]
C:\Documents and Settings\Stephen\Cookies\stephen@ads.verticalscope[1].txt [ /ads.verticalscope ]
C:\Documents and Settings\Stephen\Cookies\stephen@ads.viddler[2].txt [ /ads.viddler ]
C:\Documents and Settings\Stephen\Cookies\stephen@ads.widgetbucks[2].txt [ /ads.widgetbucks ]
C:\Documents and Settings\Stephen\Cookies\stephen@adsenserecipe[1].txt [ /adsenserecipe ]
C:\Documents and Settings\Stephen\Cookies\stephen@adserver.adtechus[1].txt [ /adserver.adtechus ]
C:\Documents and Settings\Stephen\Cookies\stephen@adserver.adtechus[2].txt [ /adserver.adtechus ]
C:\Documents and Settings\Stephen\Cookies\stephen@adtech.staticwhich.co[2].txt [ /adtech.staticwhich.co ]
C:\Documents and Settings\Stephen\Cookies\stephen@adtech.staticwhich.co[3].txt [ /adtech.staticwhich.co ]
C:\Documents and Settings\Stephen\Cookies\stephen@adtech[1].txt [ /adtech ]
C:\Documents and Settings\Stephen\Cookies\stephen@advertising[1].txt [ /advertising ]
C:\Documents and Settings\Stephen\Cookies\stephen@advertstream[2].txt [ /advertstream ]
C:\Documents and Settings\Stephen\Cookies\stephen@adviva[1].txt [ /adviva ]
C:\Documents and Settings\Stephen\Cookies\stephen@adxpose[1].txt [ /adxpose ]
C:\Documents and Settings\Stephen\Cookies\stephen@adxpose[2].txt [ /adxpose ]
C:\Documents and Settings\Stephen\Cookies\stephen@aimfar.solution.weborama[1].txt [ /aimfar.solution.weborama ]
C:\Documents and Settings\Stephen\Cookies\stephen@aimfar.solution.weborama[2].txt [ /aimfar.solution.weborama ]
C:\Documents and Settings\Stephen\Cookies\stephen@airfrance.bannerfactory[1].txt [ /airfrance.bannerfactory ]
C:\Documents and Settings\Stephen\Cookies\stephen@allyours.virginmedia[2].txt [ /allyours.virginmedia ]
C:\Documents and Settings\Stephen\Cookies\stephen@amazonmerchants.122.2o7[1].txt [ /amazonmerchants.122.2o7 ]
C:\Documents and Settings\Stephen\Cookies\stephen@amazonmerchants.122.2o7[2].txt [ /amazonmerchants.122.2o7 ]
C:\Documents and Settings\Stephen\Cookies\stephen@andomedia[1].txt [ /andomedia ]
C:\Documents and Settings\Stephen\Cookies\stephen@anrtx.tacoda[1].txt [ /anrtx.tacoda ]
C:\Documents and Settings\Stephen\Cookies\stephen@apmebf[2].txt [ /apmebf ]
C:\Documents and Settings\Stephen\Cookies\stephen@askavetquestion[2].txt [ /askavetquestion ]
C:\Documents and Settings\Stephen\Cookies\stephen@at.atwola[2].txt [ /at.atwola ]
C:\Documents and Settings\Stephen\Cookies\stephen@atdmt[1].txt [ /atdmt ]
C:\Documents and Settings\Stephen\Cookies\stephen@atdmt[3].txt [ /atdmt ]
C:\Documents and Settings\Stephen\Cookies\stephen@audience2media[1].txt [ /audience2media ]
C:\Documents and Settings\Stephen\Cookies\stephen@audience2media[2].txt [ /audience2media ]
C:\Documents and Settings\Stephen\Cookies\stephen@audience2media[3].txt [ /audience2media ]
C:\Documents and Settings\Stephen\Cookies\stephen@audit.median[1].txt [ /audit.median ]
C:\Documents and Settings\Stephen\Cookies\stephen@azjmp[2].txt [ /azjmp ]
C:\Documents and Settings\Stephen\Cookies\stephen@baa.solution.weborama[2].txt [ /baa.solution.weborama ]
C:\Documents and Settings\Stephen\Cookies\stephen@banners.bgmaps[2].txt [ /banners.bgmaps ]
C:\Documents and Settings\Stephen\Cookies\stephen@bannersng.yell[1].txt [ /bannersng.yell ]
C:\Documents and Settings\Stephen\Cookies\stephen@bannersng.yell[2].txt [ /bannersng.yell ]
C:\Documents and Settings\Stephen\Cookies\stephen@bittorrent.click-new-download[1].txt [ /bittorrent.click-new-download ]
C:\Documents and Settings\Stephen\Cookies\stephen@bizrate[1].txt [ /bizrate ]
C:\Documents and Settings\Stephen\Cookies\stephen@bluestreak[2].txt [ /bluestreak ]
C:\Documents and Settings\Stephen\Cookies\stephen@bmuk.burstnet[2].txt [ /bmuk.burstnet ]
C:\Documents and Settings\Stephen\Cookies\stephen@bmuk.burstnet[3].txt [ /bmuk.burstnet ]
C:\Documents and Settings\Stephen\Cookies\stephen@bookdiscountlinks.blogspot[1].txt [ /bookdiscountlinks.blogspot ]
C:\Documents and Settings\Stephen\Cookies\stephen@bravenet[2].txt [ /bravenet ]
C:\Documents and Settings\Stephen\Cookies\stephen@bravenet[3].txt [ /bravenet ]
C:\Documents and Settings\Stephen\Cookies\stephen@britannia.112.2o7[1].txt [ /britannia.112.2o7 ]
C:\Documents and Settings\Stephen\Cookies\stephen@bs.serving-sys[1].txt [ /bs.serving-sys ]
C:\Documents and Settings\Stephen\Cookies\stephen@bs.serving-sys[2].txt [ /bs.serving-sys ]
C:\Documents and Settings\Stephen\Cookies\stephen@burstbeacon[2].txt [ /burstbeacon ]
C:\Documents and Settings\Stephen\Cookies\stephen@burstnet[1].txt [ /burstnet ]
C:\Documents and Settings\Stephen\Cookies\stephen@burstnet[2].txt [ /burstnet ]
C:\Documents and Settings\Stephen\Cookies\stephen@c.gigcount[2].txt [ /c.gigcount ]
C:\Documents and Settings\Stephen\Cookies\stephen@care2.112.2o7[1].txt [ /care2.112.2o7 ]
C:\Documents and Settings\Stephen\Cookies\stephen@carsparefinder.co[1].txt [ /carsparefinder.co ]
C:\Documents and Settings\Stephen\Cookies\stephen@casalemedia[2].txt [ /casalemedia ]
C:\Documents and Settings\Stephen\Cookies\stephen@casalemedia[3].txt [ /casalemedia ]
C:\Documents and Settings\Stephen\Cookies\stephen@click.cashengines[2].txt [ /click.cashengines ]
C:\Documents and Settings\Stephen\Cookies\stephen@click.fspeletters[1].txt [ /click.fspeletters ]
C:\Documents and Settings\Stephen\Cookies\stephen@click.fspeletters[2].txt [ /click.fspeletters ]
C:\Documents and Settings\Stephen\Cookies\stephen@click.fspeletters[4].txt [ /click.fspeletters ]
C:\Documents and Settings\Stephen\Cookies\stephen@click.jobsgopublic[1].txt [ /click.jobsgopublic ]
C:\Documents and Settings\Stephen\Cookies\stephen@click.jobsgopublic[2].txt [ /click.jobsgopublic ]
C:\Documents and Settings\Stephen\Cookies\stephen@click.mediadome[1].txt [ /click.mediadome ]
C:\Documents and Settings\Stephen\Cookies\stephen@click2.cashengines[2].txt [ /click2.cashengines ]
C:\Documents and Settings\Stephen\Cookies\stephen@clickbank[1].txt [ /clickbank ]
C:\Documents and Settings\Stephen\Cookies\stephen@clicks.laterooms[2].txt [ /clicks.laterooms ]
C:\Documents and Settings\Stephen\Cookies\stephen@clicks.laterooms[3].txt [ /clicks.laterooms ]
C:\Documents and Settings\Stephen\Cookies\stephen@clicktrk.laterooms[2].txt [ /clicktrk.laterooms ]
C:\Documents and Settings\Stephen\Cookies\stephen@clicktrk.laterooms[3].txt [ /clicktrk.laterooms ]
C:\Documents and Settings\Stephen\Cookies\stephen@collective-media[1].txt [ /collective-media ]
C:\Documents and Settings\Stephen\Cookies\stephen@collective-media[3].txt [ /collective-media ]
C:\Documents and Settings\Stephen\Cookies\stephen@collective-media[4].txt [ /collective-media ]
C:\Documents and Settings\Stephen\Cookies\stephen@condenast.112.2o7[1].txt [ /condenast.112.2o7 ]
C:\Documents and Settings\Stephen\Cookies\stephen@content.yieldmanager[2].txt [ /content.yieldmanager ]
C:\Documents and Settings\Stephen\Cookies\stephen@content.yieldmanager[4].txt [ /content.yieldmanager ]
C:\Documents and Settings\Stephen\Cookies\stephen@counter.hitslink[1].txt [ /counter.hitslink ]
C:\Documents and Settings\Stephen\Cookies\stephen@counter2.hitslink[1].txt [ /counter2.hitslink ]
C:\Documents and Settings\Stephen\Cookies\stephen@countercentral[1].txt [ /countercentral ]
C:\Documents and Settings\Stephen\Cookies\stephen@counters.gigya[1].txt [ /counters.gigya ]
C:\Documents and Settings\Stephen\Cookies\stephen@countrywidegrounds[1].txt [ /countrywidegrounds ]
C:\Documents and Settings\Stephen\Cookies\stephen@crackyoureggprogram[2].txt [ /crackyoureggprogram ]
C:\Documents and Settings\Stephen\Cookies\stephen@dc.tremormedia[1].txt [ /dc.tremormedia ]
C:\Documents and Settings\Stephen\Cookies\stephen@directtrack[1].txt [ /directtrack ]
C:\Documents and Settings\Stephen\Cookies\stephen@discountshoestore.co[1].txt [ /discountshoestore.co ]
C:\Documents and Settings\Stephen\Cookies\stephen@discountvitaminsandherbs[2].txt [ /discountvitaminsandherbs ]
C:\Documents and Settings\Stephen\Cookies\stephen@divx.112.2o7[1].txt [ /divx.112.2o7 ]
C:\Documents and Settings\Stephen\Cookies\stephen@dmtracker[1].txt [ /dmtracker ]
C:\Documents and Settings\Stephen\Cookies\stephen@dmtracker[2].txt [ /dmtracker ]
C:\Documents and Settings\Stephen\Cookies\stephen@dmtracker[3].txt [ /dmtracker ]
C:\Documents and Settings\Stephen\Cookies\stephen@doubleclick[1].txt [ /doubleclick ]
C:\Documents and Settings\Stephen\Cookies\stephen@doubleclick[2].txt [ /doubleclick ]
C:\Documents and Settings\Stephen\Cookies\stephen@e-2dj6aekicnajkdp.stats.esomniture[2].txt [ /e-2dj6aekicnajkdp.stats.esomniture ]
C:\Documents and Settings\Stephen\Cookies\stephen@e-2dj6aekioncjkcq.stats.esomniture[2].txt [ /e-2dj6aekioncjkcq.stats.esomniture ]
C:\Documents and Settings\Stephen\Cookies\stephen@e-2dj6aelisjc5afp.stats.esomniture[2].txt [ /e-2dj6aelisjc5afp.stats.esomniture ]
C:\Documents and Settings\Stephen\Cookies\stephen@e-2dj6wal4akajikp.stats.esomniture[2].txt [ /e-2dj6wal4akajikp.stats.esomniture ]
C:\Documents and Settings\Stephen\Cookies\stephen@e-2dj6walyciczwho.stats.esomniture[1].txt [ /e-2dj6walyciczwho.stats.esomniture ]
C:\Documents and Settings\Stephen\Cookies\stephen@e-2dj6wdl4godjokq.stats.esomniture[1].txt [ /e-2dj6wdl4godjokq.stats.esomniture ]
C:\Documents and Settings\Stephen\Cookies\stephen@e-2dj6wdmyapazwgp.stats.esomniture[2].txt [ /e-2dj6wdmyapazwgp.stats.esomniture ]
C:\Documents and Settings\Stephen\Cookies\stephen@e-2dj6wfkielc5eeo.stats.esomniture[2].txt [ /e-2dj6wfkielc5eeo.stats.esomniture ]
C:\Documents and Settings\Stephen\Cookies\stephen@e-2dj6wfkoklcjscp.stats.esomniture[2].txt [ /e-2dj6wfkoklcjscp.stats.esomniture ]
C:\Documents and Settings\Stephen\Cookies\stephen@e-2dj6wglywgczabp.stats.esomniture[2].txt [ /e-2dj6wglywgczabp.stats.esomniture ]
C:\Documents and Settings\Stephen\Cookies\stephen@e-2dj6wjkokgc5kaq.stats.esomniture[2].txt [ /e-2dj6wjkokgc5kaq.stats.esomniture ]
C:\Documents and Settings\Stephen\Cookies\stephen@e-2dj6wjkygndzido.stats.esomniture[2].txt [ /e-2dj6wjkygndzido.stats.esomniture ]
C:\Documents and Settings\Stephen\Cookies\stephen@e-2dj6wjloqjajsdo.stats.esomniture[1].txt [ /e-2dj6wjloqjajsdo.stats.esomniture ]
C:\Documents and Settings\Stephen\Cookies\stephen@e-2dj6wjlyggcpekq.stats.esomniture[1].txt [ /e-2dj6wjlyggcpekq.stats.esomniture ]
C:\Documents and Settings\Stephen\Cookies\stephen@e-2dj6wmmighcjoko.stats.esomniture[1].txt [ /e-2dj6wmmighcjoko.stats.esomniture ]
C:\Documents and Settings\Stephen\Cookies\stephen@e-2dj6wnkyggd5oko.stats.esomniture[2].txt [ /e-2dj6wnkyggd5oko.stats.esomniture ]
C:\Documents and Settings\Stephen\Cookies\stephen@e-2dj6wnmyqnc5sdq.stats.esomniture[1].txt [ /e-2dj6wnmyqnc5sdq.stats.esomniture ]
C:\Documents and Settings\Stephen\Cookies\stephen@eas.apm.emediate[2].txt [ /eas.apm.emediate ]
C:\Documents and Settings\Stephen\Cookies\stephen@eas.apm.emediate[3].txt [ /eas.apm.emediate ]
C:\Documents and Settings\Stephen\Cookies\stephen@eas.apm.emediate[4].txt [ /eas.apm.emediate ]
C:\Documents and Settings\Stephen\Cookies\stephen@ehg-tfl.hitbox[2].txt [ /ehg-tfl.hitbox ]
C:\Documents and Settings\Stephen\Cookies\stephen@emediate[2].txt [ /emediate ]
C:\Documents and Settings\Stephen\Cookies\stephen@emediate[3].txt [ /emediate ]
C:\Documents and Settings\Stephen\Cookies\stephen@emediate[4].txt [ /emediate ]
C:\Documents and Settings\Stephen\Cookies\stephen@enhance[2].txt [ /enhance ]
C:\Documents and Settings\Stephen\Cookies\stephen@euroclick[1].txt [ /euroclick ]
C:\Documents and Settings\Stephen\Cookies\stephen@euroclick[2].txt [ /euroclick ]
C:\Documents and Settings\Stephen\Cookies\stephen@eventbrite.122.2o7[1].txt [ /eventbrite.122.2o7 ]
C:\Documents and Settings\Stephen\Cookies\stephen@eventbrite.122.2o7[2].txt [ /eventbrite.122.2o7 ]
C:\Documents and Settings\Stephen\Cookies\stephen@everyclick[1].txt [ /everyclick ]
C:\Documents and Settings\Stephen\Cookies\stephen@eyewonder[2].txt [ /eyewonder ]
C:\Documents and Settings\Stephen\Cookies\stephen@eyewonder[3].txt [ /eyewonder ]
C:\Documents and Settings\Stephen\Cookies\stephen@fastclick[2].txt [ /fastclick ]
C:\Documents and Settings\Stephen\Cookies\stephen@find.myrecipes[2].txt [ /find.myrecipes ]
C:\Documents and Settings\Stephen\Cookies\stephen@findaspring[1].txt [ /findaspring ]
C:\Documents and Settings\Stephen\Cookies\stephen@findaspring[2].txt [ /findaspring ]
C:\Documents and Settings\Stephen\Cookies\stephen@findhorn[1].txt [ /findhorn ]
C:\Documents and Settings\Stephen\Cookies\stephen@findingjoymovie[1].txt [ /findingjoymovie ]
C:\Documents and Settings\Stephen\Cookies\stephen@fr.at.atwola[1].txt [ /fr.at.atwola ]
C:\Documents and Settings\Stephen\Cookies\stephen@friendlytrack[2].txt [ /friendlytrack ]
C:\Documents and Settings\Stephen\Cookies\stephen@googleads.g.doubleclick[1].txt [ /googleads.g.doubleclick ]
C:\Documents and Settings\Stephen\Cookies\stephen@guyfinley.directtrack[2].txt [ /guyfinley.directtrack ]
C:\Documents and Settings\Stephen\Cookies\stephen@hearstmagazines.112.2o7[1].txt [ /hearstmagazines.112.2o7 ]
C:\Documents and Settings\Stephen\Cookies\stephen@herbdoc.112.2o7[1].txt [ /herbdoc.112.2o7 ]
C:\Documents and Settings\Stephen\Cookies\stephen@hitbox[2].txt [ /hitbox ]
C:\Documents and Settings\Stephen\Cookies\stephen@ilead.itrack[1].txt [ /ilead.itrack ]
C:\Documents and Settings\Stephen\Cookies\stephen@imrworldwide[2].txt [ /imrworldwide ]
C:\Documents and Settings\Stephen\Cookies\stephen@imrworldwide[3].txt [ /imrworldwide ]
C:\Documents and Settings\Stephen\Cookies\stephen@imrworldwide[4].txt [ /imrworldwide ]
C:\Documents and Settings\Stephen\Cookies\stephen@in.getclicky[1].txt [ /in.getclicky ]
C:\Documents and Settings\Stephen\Cookies\stephen@in.getclicky[2].txt [ /in.getclicky ]
C:\Documents and Settings\Stephen\Cookies\stephen@insightexpressai[1].txt [ /insightexpressai ]
C:\Documents and Settings\Stephen\Cookies\stephen@interclick[1].txt [ /interclick ]
C:\Documents and Settings\Stephen\Cookies\stephen@invitemedia[1].txt [ /invitemedia ]
C:\Documents and Settings\Stephen\Cookies\stephen@kantarmedia[2].txt [ /kantarmedia ]
C:\Documents and Settings\Stephen\Cookies\stephen@kiddicare.solution.weborama[2].txt [ /kiddicare.solution.weborama ]
C:\Documents and Settings\Stephen\Cookies\stephen@kontera[1].txt [ /kontera ]
C:\Documents and Settings\Stephen\Cookies\stephen@kontera[2].txt [ /kontera ]
C:\Documents and Settings\Stephen\Cookies\stephen@latestnews.virginmedia[1].txt [ /latestnews.virginmedia ]
C:\Documents and Settings\Stephen\Cookies\stephen@legolas-media[2].txt [ /legolas-media ]
C:\Documents and Settings\Stephen\Cookies\stephen@lfstmedia[1].txt [ /lfstmedia ]
C:\Documents and Settings\Stephen\Cookies\stephen@lfstmedia[2].txt [ /lfstmedia ]
C:\Documents and Settings\Stephen\Cookies\stephen@liveperson[1].txt [ /liveperson ]
C:\Documents and Settings\Stephen\Cookies\stephen@liveperson[3].txt [ /liveperson ]
C:\Documents and Settings\Stephen\Cookies\stephen@liveperson[4].txt [ /liveperson ]
C:\Documents and Settings\Stephen\Cookies\stephen@liveperson[5].txt [ /liveperson ]
C:\Documents and Settings\Stephen\Cookies\stephen@lstat.youku[2].txt [ /lstat.youku ]
C:\Documents and Settings\Stephen\Cookies\stephen@lucidmedia[2].txt [ /lucidmedia ]
C:\Documents and Settings\Stephen\Cookies\stephen@measussex.org[2].txt [ /measussex.org ]
C:\Documents and Settings\Stephen\Cookies\stephen@media.cardomain[1].txt [ /media.cardomain ]
C:\Documents and Settings\Stephen\Cookies\stephen@media.easyads[2].txt [ /media.easyads ]
C:\Documents and Settings\Stephen\Cookies\stephen@media.medhelp[1].txt [ /media.medhelp ]
C:\Documents and Settings\Stephen\Cookies\stephen@media.medhelp[3].txt [ /media.medhelp ]
C:\Documents and Settings\Stephen\Cookies\stephen@media.mercola[2].txt [ /media.mercola ]
C:\Documents and Settings\Stephen\Cookies\stephen@media6degrees[1].txt [ /media6degrees ]
C:\Documents and Settings\Stephen\Cookies\stephen@media6degrees[3].txt [ /media6degrees ]
C:\Documents and Settings\Stephen\Cookies\stephen@media6degrees[4].txt [ /media6degrees ]
C:\Documents and Settings\Stephen\Cookies\stephen@mediabrandsww[1].txt [ /mediabrandsww ]
C:\Documents and Settings\Stephen\Cookies\stephen@mediaforge[1].txt [ /mediaforge ]
C:\Documents and Settings\Stephen\Cookies\stephen@mediaplex[2].txt [ /mediaplex ]
C:\Documents and Settings\Stephen\Cookies\stephen@mediaweb.musicradio[1].txt [ /mediaweb.musicradio ]
C:\Documents and Settings\Stephen\Cookies\stephen@mercola.122.2o7[1].txt [ /mercola.122.2o7 ]
C:\Documents and Settings\Stephen\Cookies\stephen@microsoftsto.112.2o7[1].txt [ /microsoftsto.112.2o7 ]
C:\Documents and Settings\Stephen\Cookies\stephen@mm.chitika[2].txt [ /mm.chitika ]
C:\Documents and Settings\Stephen\Cookies\stephen@mm.chitika[3].txt [ /mm.chitika ]
C:\Documents and Settings\Stephen\Cookies\stephen@movies.virginmedia[1].txt [ /movies.virginmedia ]
C:\Documents and Settings\Stephen\Cookies\stephen@msnportal.112.2o7[1].txt [ /msnportal.112.2o7 ]
C:\Documents and Settings\Stephen\Cookies\stephen@msnportal.112.2o7[2].txt [ /msnportal.112.2o7 ]
C:\Documents and Settings\Stephen\Cookies\stephen@mtvn.112.2o7[1].txt [ /mtvn.112.2o7 ]
C:\Documents and Settings\Stephen\Cookies\stephen@mywebsearch[1].txt [ /mywebsearch ]
C:\Documents and Settings\Stephen\Cookies\stephen@naturalfoodfinder.co[1].txt [ /naturalfoodfinder.co ]
C:\Documents and Settings\Stephen\Cookies\stephen@naturalfoodfinder.co[2].txt [ /naturalfoodfinder.co ]
C:\Documents and Settings\Stephen\Cookies\stephen@naturalfoodfinder.co[4].txt [ /naturalfoodfinder.co ]
C:\Documents and Settings\Stephen\Cookies\stephen@oneclickpharmacy.co[2].txt [ /oneclickpharmacy.co ]
C:\Documents and Settings\Stephen\Cookies\stephen@onlineadtracker.co[2].txt [ /onlineadtracker.co ]
C:\Documents and Settings\Stephen\Cookies\stephen@optimize.indieclick[2].txt [ /optimize.indieclick ]
C:\Documents and Settings\Stephen\Cookies\stephen@oracle.112.2o7[1].txt [ /oracle.112.2o7 ]
C:\Documents and Settings\Stephen\Cookies\stephen@paypal.112.2o7[2].txt [ /paypal.112.2o7 ]
C:\Documents and Settings\Stephen\Cookies\stephen@paypal.112.2o7[3].txt [ /paypal.112.2o7 ]
C:\Documents and Settings\Stephen\Cookies\stephen@popuptraffic[1].txt [ /popuptraffic ]
C:\Documents and Settings\Stephen\Cookies\stephen@pro-market[2].txt [ /pro-market ]
C:\Documents and Settings\Stephen\Cookies\stephen@pro-market[3].txt [ /pro-market ]
C:\Documents and Settings\Stephen\Cookies\stephen@propertyfinder[1].txt [ /propertyfinder ]
C:\Documents and Settings\Stephen\Cookies\stephen@propertyfinder[2].txt [ /propertyfinder ]
C:\Documents and Settings\Stephen\Cookies\stephen@questionmarket[1].txt [ /questionmarket ]
C:\Documents and Settings\Stephen\Cookies\stephen@quote.airport-parking-discounts.co[2].txt [ /quote.airport-parking-discounts.co ]
C:\Documents and Settings\Stephen\Cookies\stephen@r1-ads.ace.advertising[2].txt [ /r1-ads.ace.advertising ]
C:\Documents and Settings\Stephen\Cookies\stephen@r1-ads.ace.advertising[3].txt [ /r1-ads.ace.advertising ]
C:\Documents and Settings\Stephen\Cookies\stephen@realmedia[2].txt [ /realmedia ]
C:\Documents and Settings\Stephen\Cookies\stephen@revsci[1].txt [ /revsci ]
C:\Documents and Settings\Stephen\Cookies\stephen@revsci[2].txt [ /revsci ]
C:\Documents and Settings\Stephen\Cookies\stephen@rts.pgmediaserve[1].txt [ /rts.pgmediaserve ]
C:\Documents and Settings\Stephen\Cookies\stephen@ru4[2].txt [ /ru4 ]
C:\Documents and Settings\Stephen\Cookies\stephen@ru4[3].txt [ /ru4 ]
C:\Documents and Settings\Stephen\Cookies\stephen@search.virginmedia[2].txt [ /search.virginmedia ]
C:\Documents and Settings\Stephen\Cookies\stephen@server.lon.liveperson[2].txt [ /server.lon.liveperson ]
C:\Documents and Settings\Stephen\Cookies\stephen@server.lon.liveperson[3].txt [ /server.lon.liveperson ]
C:\Documents and Settings\Stephen\Cookies\stephen@serving-sys[1].txt [ /serving-sys ]
C:\Documents and Settings\Stephen\Cookies\stephen@smartadserver[2].txt [ /smartadserver ]
C:\Documents and Settings\Stephen\Cookies\stephen@socialmedia[1].txt [ /socialmedia ]
C:\Documents and Settings\Stephen\Cookies\stephen@specificclick[1].txt [ /specificclick ]
C:\Documents and Settings\Stephen\Cookies\stephen@specificclick[2].txt [ /specificclick ]
C:\Documents and Settings\Stephen\Cookies\stephen@spicesofindia.co[2].txt [ /spicesofindia.co ]
C:\Documents and Settings\Stephen\Cookies\stephen@stat.aldi[1].txt [ /stat.aldi ]
C:\Documents and Settings\Stephen\Cookies\stephen@stat.dealtime[1].txt [ /stat.dealtime ]
C:\Documents and Settings\Stephen\Cookies\stephen@stat.dealtime[3].txt [ /stat.dealtime ]
C:\Documents and Settings\Stephen\Cookies\stephen@stat.youku[1].txt [ /stat.youku ]
C:\Documents and Settings\Stephen\Cookies\stephen@statcounter[1].txt [ /statcounter ]
C:\Documents and Settings\Stephen\Cookies\stephen@statcounter[3].txt [ /statcounter ]
C:\Documents and Settings\Stephen\Cookies\stephen@stats.dnnmetrics[1].txt [ /stats.dnnmetrics ]
C:\Documents and Settings\Stephen\Cookies\stephen@stats.free-rein[1].txt [ /stats.free-rein ]
C:\Documents and Settings\Stephen\Cookies\stephen@stats.manticoretechnology[1].txt [ /stats.manticoretechnology ]
C:\Documents and Settings\Stephen\Cookies\stephen@stats.matraxis[1].txt [ /stats.matraxis ]
C:\Documents and Settings\Stephen\Cookies\stephen@stats.matraxis[2].txt [ /stats.matraxis ]
C:\Documents and Settings\Stephen\Cookies\stephen@stats.matraxis[3].txt [ /stats.matraxis ]
C:\Documents and Settings\Stephen\Cookies\stephen@stats.mytraveline[2].txt [ /stats.mytraveline ]
C:\Documents and Settings\Stephen\Cookies\stephen@stats.paypal[2].txt [ /stats.paypal ]
C:\Documents and Settings\Stephen\Cookies\stephen@stats.paypal[3].txt [ /stats.paypal ]
C:\Documents and Settings\Stephen\Cookies\stephen@stats.paypal[4].txt [ /stats.paypal ]
C:\Documents and Settings\Stephen\Cookies\stephen@statse.webtrendslive[2].txt [ /statse.webtrendslive ]
C:\Documents and Settings\Stephen\Cookies\stephen@steelhousemedia[2].txt [ /steelhousemedia ]
C:\Documents and Settings\Stephen\Cookies\stephen@steenbergs.co[1].txt [ /steenbergs.co ]
C:\Documents and Settings\Stephen\Cookies\stephen@steenbergs.co[2].txt [ /steenbergs.co ]
C:\Documents and Settings\Stephen\Cookies\stephen@steenbergs.co[3].txt [ /steenbergs.co ]
C:\Documents and Settings\Stephen\Cookies\stephen@superstats[1].txt [ /superstats ]
C:\Documents and Settings\Stephen\Cookies\stephen@surveymonkey.122.2o7[1].txt [ /surveymonkey.122.2o7 ]
C:\Documents and Settings\Stephen\Cookies\stephen@tacoda.at.atwola[1].txt [ /tacoda.at.atwola ]
C:\Documents and Settings\Stephen\Cookies\stephen@tacoda.at.atwola[3].txt [ /tacoda.at.atwola ]
C:\Documents and Settings\Stephen\Cookies\stephen@target.tangomedia.co[2].txt [ /target.tangomedia.co ]
C:\Documents and Settings\Stephen\Cookies\stephen@thefind.co[2].txt [ /thefind.co ]
C:\Documents and Settings\Stephen\Cookies\stephen@tiscali.propertyfinder[1].txt [ /tiscali.propertyfinder ]
C:\Documents and Settings\Stephen\Cookies\stephen@toplist[2].txt [ /toplist ]
C:\Documents and Settings\Stephen\Cookies\stephen@track.adform[2].txt [ /track.adform ]
C:\Documents and Settings\Stephen\Cookies\stephen@track.omguk[1].txt [ /track.omguk ]
C:\Documents and Settings\Stephen\Cookies\stephen@track.omguk[3].txt [ /track.omguk ]
C:\Documents and Settings\Stephen\Cookies\stephen@tracker.roitesting[1].txt [ /tracker.roitesting ]
C:\Documents and Settings\Stephen\Cookies\stephen@tracker.roitesting[2].txt [ /tracker.roitesting ]
C:\Documents and Settings\Stephen\Cookies\stephen@tracking.dc-storm[2].txt [ /tracking.dc-storm ]
C:\Documents and Settings\Stephen\Cookies\stephen@tracking.liveyourtruth[1].txt [ /tracking.liveyourtruth ]
C:\Documents and Settings\Stephen\Cookies\stephen@tracking.summitmedia.co[1].txt [ /tracking.summitmedia.co ]
C:\Documents and Settings\Stephen\Cookies\stephen@tracking.vcab[2].txt [ /tracking.vcab ]
C:\Documents and Settings\Stephen\Cookies\stephen@tradedoubler[2].txt [ /tradedoubler ]
C:\Documents and Settings\Stephen\Cookies\stephen@trafficking.nabbr[2].txt [ /trafficking.nabbr ]
C:\Documents and Settings\Stephen\Cookies\stephen@trafficmp[2].txt [ /trafficmp ]
C:\Documents and Settings\Stephen\Cookies\stephen@tribalfusion[1].txt [ /tribalfusion ]
C:\Documents and Settings\Stephen\Cookies\stephen@tuiactivity.112.2o7[1].txt [ /tuiactivity.112.2o7 ]
C:\Documents and Settings\Stephen\Cookies\stephen@tvguide.virginmedia[2].txt [ /tvguide.virginmedia ]
C:\Documents and Settings\Stephen\Cookies\stephen@uk.at.atwola[1].txt [ /uk.at.atwola ]
C:\Documents and Settings\Stephen\Cookies\stephen@user.lucidmedia[1].txt [ /user.lucidmedia ]
C:\Documents and Settings\Stephen\Cookies\stephen@virginmedia[1].txt [ /virginmedia ]
C:\Documents and Settings\Stephen\Cookies\stephen@virginmedia[2].txt [ /virginmedia ]
C:\Documents and Settings\Stephen\Cookies\stephen@w3counter[2].txt [ /w3counter ]
C:\Documents and Settings\Stephen\Cookies\stephen@weather.virginmedia[1].txt [ /weather.virginmedia ]
C:\Documents and Settings\Stephen\Cookies\stephen@weborama[1].txt [ /weborama ]
C:\Documents and Settings\Stephen\Cookies\stephen@worldnakedbikeride[2].txt [ /worldnakedbikeride ]
C:\Documents and Settings\Stephen\Cookies\stephen@
www.burstbeacon[2].txt [ /www.burstbeacon ]
C:\Documents and Settings\Stephen\Cookies\stephen@
www.burstbeacon[3].txt [ /www.burstbeacon ]
C:\Documents and Settings\Stephen\Cookies\stephen@
www.burstnet[1].txt [ /www.burstnet ]
C:\Documents and Settings\Stephen\Cookies\stephen@
www.burstnet[2].txt [ /www.burstnet ]
C:\Documents and Settings\Stephen\Cookies\stephen@
www.burstnet[4].txt [ /www.burstnet ]
C:\Documents and Settings\Stephen\Cookies\stephen@
www.burstnet[5].txt [ /www.burstnet ]
C:\Documents and Settings\Stephen\Cookies\stephen@
www.burstnet[6].txt [ /www.burstnet ]
C:\Documents and Settings\Stephen\Cookies\stephen@
www.clicksafe.lloydstsb[1].txt [ /www.clicksafe.lloydstsb ]
C:\Documents and Settings\Stephen\Cookies\stephen@
www.clicksafe.lloydstsb[2].txt [ /www.clicksafe.lloydstsb ]
C:\Documents and Settings\Stephen\Cookies\stephen@
www.clicksafe.lloydstsb[4].txt [ /www.clicksafe.lloydstsb ]
C:\Documents and Settings\Stephen\Cookies\stephen@
www.clicktoviewlink[1].txt [ /www.clicktoviewlink ]
C:\Documents and Settings\Stephen\Cookies\stephen@
www.countryside-jobs[1].txt [ /www.countryside-jobs ]
C:\Documents and Settings\Stephen\Cookies\stephen@
www.countryside-jobs[2].txt [ /www.countryside-jobs ]
C:\Documents and Settings\Stephen\Cookies\stephen@
www.countryside-jobs[3].txt [ /www.countryside-jobs ]
C:\Documents and Settings\Stephen\Cookies\stephen@
www.discountshoestore.co[1].txt [ /www.discountshoestore.co ]
C:\Documents and Settings\Stephen\Cookies\stephen@
www.dover-parking-discounts.co[2].txt [ /www.dover-parking-discounts.co ]
C:\Documents and Settings\Stephen\Cookies\stephen@
www.everyclick[1].txt [ /www.everyclick ]
C:\Documents and Settings\Stephen\Cookies\stephen@
www.findingjoymovie[1].txt [ /www.findingjoymovie ]
C:\Documents and Settings\Stephen\Cookies\stephen@
www.googleadservices[11].txt [ /www.googleadservices ]
C:\Documents and Settings\Stephen\Cookies\stephen@
www.googleadservices[1].txt [ /www.googleadservices ]
C:\Documents and Settings\Stephen\Cookies\stephen@
www.googleadservices[2].txt [ /www.googleadservices ]
C:\Documents and Settings\Stephen\Cookies\stephen@
www.googleadservices[3].txt [ /www.googleadservices ]
C:\Documents and Settings\Stephen\Cookies\stephen@
www.googleadservices[4].txt [ /www.googleadservices ]
C:\Documents and Settings\Stephen\Cookies\stephen@
www.googleadservices[5].txt [ /www.googleadservices ]
C:\Documents and Settings\Stephen\Cookies\stephen@
www.googleadservices[6].txt [ /www.googleadservices ]
C:\Documents and Settings\Stephen\Cookies\stephen@
www.googleadservices[7].txt [ /www.googleadservices ]
C:\Documents and Settings\Stephen\Cookies\stephen@
www.grapeshot-media[1].txt [ /www.grapeshot-media ]
C:\Documents and Settings\Stephen\Cookies\stephen@
www.hardtofindseminars[2].txt [ /www.hardtofindseminars ]
C:\Documents and Settings\Stephen\Cookies\stephen@
www.hxtrack[1].txt [ /www.hxtrack ]
C:\Documents and Settings\Stephen\Cookies\stephen@
www.ist-track[1].txt [ /www.ist-track ]
C:\Documents and Settings\Stephen\Cookies\stephen@
www.measussex.org[1].txt [ /www.measussex.org ]
C:\Documents and Settings\Stephen\Cookies\stephen@
www.onetruemedia[1].txt [ /www.onetruemedia ]
C:\Documents and Settings\Stephen\Cookies\stephen@
www.petmedia.co[2].txt [ /www.petmedia.co ]
C:\Documents and Settings\Stephen\Cookies\stephen@
www.stats.tso.co[1].txt [ /www.stats.tso.co ]
C:\Documents and Settings\Stephen\Cookies\stephen@
www.stats.tso.co[2].txt [ /www.stats.tso.co ]
C:\Documents and Settings\Stephen\Cookies\stephen@
www.steenbergs.co[1].txt [ /www.steenbergs.co ]
C:\Documents and Settings\Stephen\Cookies\stephen@
www.sublimemedia[1].txt [ /www.sublimemedia ]
C:\Documents and Settings\Stephen\Cookies\stephen@
www.thefind.co[1].txt [ /www.thefind.co ]
C:\Documents and Settings\Stephen\Cookies\stephen@
www.virginmedia[1].txt [ /www.virginmedia ]
C:\Documents and Settings\Stephen\Cookies\stephen@
www.virginmedia[2].txt [ /www.virginmedia ]
C:\Documents and Settings\Stephen\Cookies\stephen@xiti[1].txt [ /xiti ]
C:\Documents and Settings\Stephen\Cookies\stephen@xiti[2].txt [ /xiti ]
C:\Documents and Settings\Stephen\Cookies\stephen@xiti[3].txt [ /xiti ]
C:\Documents and Settings\Stephen\Cookies\stephen@xm.xtendmedia[1].txt [ /xm.xtendmedia ]
C:\Documents and Settings\Stephen\Cookies\stephen@yadro[1].txt [ /yadro ]
C:\Documents and Settings\Stephen\Cookies\stephen@yourcounty.co[1].txt [ /yourcounty.co ]
C:\Documents and Settings\Stephen\Cookies\stephen@zedo[1].txt [ /zedo ]
C:\Documents and Settings\Stephen\Cookies\ZLUCGGPX.txt [ /media.mercola.com ]
C:\Documents and Settings\Stephen\Cookies\EUJNT3NW.txt [ /interclick.com ]
C:\Documents and Settings\Stephen\Cookies\6O9RURKM.txt [ /delivery.ads-littlestarmedia.co.uk ]
C:\Documents and Settings\Stephen\Cookies\D8MCF4LZ.txt [ /questionmarket.com ]
C:\Documents and Settings\Stephen\Cookies\7RBZ9CY7.txt [ /mediaservices-d.openxenterprise.com ]
C:\Documents and Settings\Stephen\Cookies\66QW8P3N.txt [ /ad.yieldmanager.com ]
C:\Documents and Settings\Stephen\Cookies\BJOWQJPC.txt [ /gnosticmedia.com ]
C:\Documents and Settings\Stephen\Cookies\OY68EX60.txt [ /www.googleadservices.com ]
C:\Documents and Settings\Stephen\Cookies\S3VTVX07.txt [ /tracking.3gnet.de ]
C:\Documents and Settings\Stephen\Cookies\FC68IJD6.txt [ /legolas-media.com ]
C:\Documents and Settings\Stephen\Cookies\0GBEM90R.txt [ /2o7.net ]
C:\Documents and Settings\Stephen\Cookies\YEW9YKTC.txt [ /invitemedia.com ]
C:\Documents and Settings\Stephen\Cookies\FJCOO34X.txt [ /virginmedia.com ]
C:\Documents and Settings\Stephen\Cookies\VORMJKGR.txt [ /media6degrees.com ]
C:\Documents and Settings\Stephen\Cookies\5FTN808R.txt [ /adtech.de ]
C:\Documents and Settings\Stephen\Cookies\I8LML8P8.txt [ /e-2dj6aekococ5odq.stats.esomniture.com ]
C:\Documents and Settings\Stephen\Cookies\8CW79HDY.txt [ /burstnet.com ]
C:\Documents and Settings\Stephen\Cookies\IFM5V843.txt [ /tracker.roitesting.com ]
C:\Documents and Settings\Stephen\Cookies\7HNDII1V.txt [ /revsci.net ]
C:\Documents and Settings\Stephen\Cookies\KOOCAAC7.txt [ /in.getclicky.com ]
C:\Documents and Settings\Stephen\Cookies\G2P2JQVR.txt [ /tacoda.at.atwola.com ]
C:\Documents and Settings\Stephen\Cookies\V31FBQRS.txt [ /dmtracker.com ]
C:\Documents and Settings\Stephen\Cookies\3MZDMT97.txt [ /andomedia.com ]
C:\Documents and Settings\Stephen\Cookies\3VSVFVI8.txt [ /server.iad.liveperson.net ]
C:\Documents and Settings\Stephen\Cookies\P8AOZV07.txt [ /msnbc.112.2o7.net ]
C:\Documents and Settings\Stephen\Cookies\WJSNMMHC.txt [ /imrworldwide.com ]
C:\Documents and Settings\Stephen\Cookies\CCR7N9LC.txt [ /lucidmedia.com ]
C:\Documents and Settings\Stephen\Cookies\MYX256Z3.txt [ /at.atwola.com ]
C:\Documents and Settings\Stephen\Cookies\W8WVUCFP.txt [ /paypal.112.2o7.net ]
C:\Documents and Settings\Stephen\Cookies\PADJOJTG.txt [ /www.googleadservices.com ]
C:\Documents and Settings\Stephen\Cookies\1EDENWSQ.txt [ /doubleclick.net ]
C:\Documents and Settings\Stephen\Cookies\D59LEHMN.txt [ /serving-sys.com ]
C:\Documents and Settings\Stephen\Cookies\2K818SGT.txt [ /e-2dj6wal4akajikp.stats.esomniture.com ]
C:\Documents and Settings\Stephen\Cookies\M2RLN91W.txt [ /eas.apm.emediate.eu ]
C:\Documents and Settings\Stephen\Cookies\NL6SQ93K.txt [ /ads.undertone.com ]
C:\Documents and Settings\Stephen\Cookies\0IDJ9NB1.txt [ /www.burstnet.com ]
C:\Documents and Settings\Stephen\Cookies\3G0A5CPS.txt [ /liveperson.net ]
C:\Documents and Settings\Stephen\Cookies\0GFDJQ7O.txt [ /liveperson.net ]
C:\Documents and Settings\Stephen\Cookies\PHBZFSON.txt [ /mediaplex.com ]
C:\Documents and Settings\Stephen\Cookies\YJ3A2GTX.txt [ /statse.webtrendslive.com ]
C:\Documents and Settings\Stephen\Cookies\5YCFRG4R.txt [ /bs.serving-sys.com ]
C:\Documents and Settings\Stephen\Cookies\0C898PTC.txt [ /counter.hitslink.com ]
C:\Documents and Settings\Stephen\Cookies\988Y2864.txt [ /hc2.humanclick.com ]
C:\Documents and Settings\Stephen\Cookies\T3EY5KFL.txt [ /www.googleadservices.com ]
C:\Documents and Settings\Stephen\Cookies\HD2JCADY.txt [ /ad.360yield.com ]
C:\Documents and Settings\Stephen\Cookies\LQO7CZ9Z.txt [ /ru4.com ]
C:\Documents and Settings\Stephen\Cookies\ULHUXVB3.txt [ /atdmt.com ]
C:\Documents and Settings\Stephen\Cookies\CM4LIMIJ.txt [ /ads.pubmatic.com ]
C:\Documents and Settings\Stephen\Cookies\9HBO7XD5.txt [ /bizrate.com ]
C:\Documents and Settings\Stephen\Cookies\T5B1O5OX.txt [ /statcounter.com ]
C:\Documents and Settings\Stephen\Cookies\D7GDQZKE.txt [ /apmebf.com ]
C:\Documents and Settings\Stephen\Cookies\7TO6KKYF.txt [ /advertising.com ]
C:\Documents and Settings\Stephen\Cookies\PR5YV9TJ.txt [ /adbrite.com ]
C:\Documents and Settings\Stephen\Cookies\MKSQ3I3M.txt [ /specificclick.net ]
C:\Documents and Settings\Stephen\Cookies\UDJJO1HQ.txt [ /tribalfusion.com ]
C:\Documents and Settings\Stephen\Cookies\26LJVH3T.txt [ /stat.onestat.com ]
C:\Documents and Settings\Stephen\Cookies\DZ3D2MCS.txt [ /accounts.google.com ]
C:\Documents and Settings\Stephen\Cookies\N5P71FIA.txt [ /zedo.com ]
C:\Documents and Settings\Stephen\Cookies\TUBRUNAB.txt [ /casalemedia.com ]
C:\Documents and Settings\Stephen\Cookies\7R6JOVBI.txt [ /adviva.net ]
C:\Documents and Settings\Stephen\Cookies\E9CM4V39.txt [ /fastclick.net ]
C:\Documents and Settings\Stephen\Cookies\9MOAI84G.txt [ /www.googleadservices.com ]
C:\Documents and Settings\Stephen\Cookies\SKI5B6E3.txt [ /e-2dj6wjnyglcjckp.stats.esomniture.com ]
C:\Documents and Settings\Stephen\Cookies\M0P9BG58.txt [ /click.expandsearchanswers.com ]
C:\Documents and Settings\Stephen\Cookies\HOE3SUZB.txt [ /www.steenbergs.co.uk ]
C:\Documents and Settings\Stephen\Cookies\CAI0AW0K.txt [ /steenbergs.co.uk ]
C:\Documents and Settings\Stephen\Cookies\NSBY4JHR.txt [ /hc2.humanclick.com ]
C:\Documents and Settings\Stephen\Cookies\54Q7IS5V.txt [ /www.googleadservices.com ]
C:\Documents and Settings\Stephen\Cookies\J5F2W0HX.txt [ /ox-d.fondnessmedia.com ]
C:\Documents and Settings\Stephen\Cookies\VBAH1ILU.txt [ /adserver.adtechus.com ]
C:\Documents and Settings\Stephen\Cookies\G1JYUNM5.txt [ /uk.at.atwola.com ]
C:\Documents and Settings\Stephen\Cookies\440I8ARJ.txt [ /tradedoubler.com ]
C:\Documents and Settings\Stephen\Cookies\VQT8GKC7.txt [ /liveperson.net ]
C:\Documents and Settings\Stephen\Cookies\NX9CRI82.txt [ /network.realmedia.com ]
C:\Documents and Settings\Stephen\Cookies\U6TUVRJB.txt [ /www.googleadservices.com ]
C:\Documents and Settings\Stephen\Cookies\W7STGVJG.txt [ /rotator.adjuggler.com ]
C:\Documents and Settings\Stephen\Cookies\MHNY10HL.txt [ /realmedia.com ]
C:\Documents and Settings\Stephen\Cookies\YDKG5YL3.txt [ /audience2media.com ]
C:\Documents and Settings\Stephen\Cookies\Z0U4IBL4.txt [ /www.googleadservices.com ]
C:\Documents and Settings\Stephen\Cookies\X1JLTMWO.txt [ /xm.xtendmedia.com ]
C:\Documents and Settings\Stephen\Cookies\EQ1XSG2W.txt [ /kaspersky.122.2o7.net ]
C:\Documents and Settings\Stephen\Cookies\OX0HWOZF.txt [ /tracking.onefeed.co.uk ]
C:\Documents and Settings\Stephen\Cookies\TYS122QX.txt [ /dc.tremormedia.com ]
C:\Documents and Settings\Stephen\Cookies\ZBKONQW5.txt [ /steelhousemedia.com ]
C:\Documents and Settings\Stephen\Cookies\5GGBRHO8.txt [ /tacoda.net ]
C:\Documents and Settings\Stephen\Cookies\EEG7B7D7.txt [ /mm.chitika.net ]
C:\Documents and Settings\Stephen\Cookies\KJ1G2WW8.txt [ /www.googleadservices.com ]
C:\Documents and Settings\Stephen\Cookies\ZWB7TUHE.txt [ /googleads.g.doubleclick.net ]
C:\Documents and Settings\Stephen\Cookies\CKYQIDKM.txt [ /yadro.ru ]
C:\Documents and Settings\Stephen\Cookies\D8B3J4II.txt [ /ads.lycos.com ]
C:\Documents and Settings\Stephen\Cookies\8NB6PRD4.txt [ /adxpose.com ]
C:\Documents and Settings\Stephen\Cookies\I8JE0P6H.txt [ /smartadserver.com ]
C:\Documents and Settings\Stephen\Cookies\WC85T96I.txt [ /ad.zanox.com ]
C:\Documents and Settings\Stephen\Cookies\4PZA74CV.txt [ /amazon-adsystem.com ]
C:\Documents and Settings\Stephen\Cookies\BN6AX8RY.txt [ /ads.pointroll.com ]
C:\Documents and Settings\Stephen\Cookies\MDUSWHZ5.txt [ /pointroll.com ]
C:\Documents and Settings\Stephen\Cookies\4R9ZQZAD.txt [ /cn.clickable.net ]
C:\Documents and Settings\Stephen\Cookies\EGPQ3E9T.txt [ /collective-media.net ]
C:\Documents and Settings\Stephen\Cookies\Z5C08TX3.txt [ /ads.bleepingcomputer.com ]
C:\Documents and Settings\Stephen\Cookies\R6TOMNVY.txt [ /ads.msv-inc.com ]
C:\Documents and Settings\Stephen\Cookies\XDHP2X24.txt [ /www.clicksafe.lloydstsb.com ]
C:\Documents and Settings\Stephen\Cookies\B3TSU2RP.txt [ /eas4.emediate.eu ]
C:\Documents and Settings\Stephen\Cookies\YIMI17D6.txt [ /www.grapeshot-media.net ]
C:\Documents and Settings\Stephen\Cookies\R0YSVW4T.txt [ /armanicouture.solution.weborama.fr ]
C:\Documents and Settings\Stephen\Cookies\9N9VHOK8.txt [ /247realmedia.com ]
C:\Documents and Settings\Stephen\Cookies\PJXG18GE.txt [ /ads.saymedia.com ]
C:\Documents and Settings\Stephen\Cookies\JRYKGXAG.txt [ /weborama.fr ]
C:\Documents and Settings\Stephen\Cookies\2RHL9QT1.txt [ /pro-market.net ]
C:\Documents and Settings\Stephen\Cookies\7Z1Z5IAJ.txt [ /kontera.com ]
C:\Documents and Settings\Stephen\Cookies\V75X03RU.txt [ /www.countrycottagescotswolds.co.uk ]
C:\DOCUMENTS AND SETTINGS\ADMINISTRATOR\Cookies\HRPGHB11.txt [ Cookie:administrator@atdmt.com/ ]
C:\DOCUMENTS AND SETTINGS\ADMINISTRATOR\Cookies\QNN5TT4T.txt [ Cookie:administrator@apmebf.com/ ]
C:\DOCUMENTS AND SETTINGS\ADMINISTRATOR\Cookies\32PLDIYG.txt [ Cookie:administrator@adtech.de/ ]
C:\DOCUMENTS AND SETTINGS\ADMINISTRATOR\Cookies\BIAWNEUW.txt [ Cookie:administrator@media6degrees.com/ ]
C:\DOCUMENTS AND SETTINGS\ADMINISTRATOR\Cookies\38BLAGGW.txt [ Cookie:administrator@tradedoubler.com/ ]
C:\DOCUMENTS AND SETTINGS\ADMINISTRATOR\Cookies\HQ4P7091.txt [ Cookie:administrator@adsonar.com/adserving ]
C:\DOCUMENTS AND SETTINGS\ADMINISTRATOR\Cookies\OJ6X4H4U.txt [ Cookie:administrator@adserver.adtechus.com/ ]
C:\DOCUMENTS AND SETTINGS\ADMINISTRATOR\Cookies\A2ZZ6AM4.txt [ Cookie:administrator@ru4.com/ ]
C:\DOCUMENTS AND SETTINGS\ADMINISTRATOR\Cookies\SQKCBMFP.txt [ Cookie:administrator@adbrite.com/ ]
C:\DOCUMENTS AND SETTINGS\ADMINISTRATOR\Cookies\JN9OAQH1.txt [ Cookie:administrator@specificclick.net/ ]
C:\DOCUMENTS AND SETTINGS\ADMINISTRATOR\Cookies\Q1HRCUKW.txt [ Cookie:administrator@revsci.net/ ]
C:\DOCUMENTS AND SETTINGS\ADMINISTRATOR\Cookies\Q5CIGGPZ.txt [ Cookie:administrator@tribalfusion.com/ ]
C:\DOCUMENTS AND SETTINGS\ADMINISTRATOR\Cookies\1E9GDYPB.txt [ Cookie:administrator@tacoda.at.atwola.com/ ]
C:\DOCUMENTS AND SETTINGS\ADMINISTRATOR\Cookies\AOBLX1SK.txt [ Cookie:administrator@eas4.emediate.eu/ ]
C:\DOCUMENTS AND SETTINGS\ADMINISTRATOR\Cookies\KLEDR8KE.txt [ Cookie:administrator@at.atwola.com/ ]
C:\DOCUMENTS AND SETTINGS\ADMINISTRATOR\Cookies\3M2DI6A1.txt [ Cookie:administrator@pro-market.net/ ]
C:\DOCUMENTS AND SETTINGS\ADMINISTRATOR\Cookies\8PA9V0L0.txt [ Cookie:administrator@adxpose.com/ ]
C:\DOCUMENTS AND SETTINGS\ADMINISTRATOR\Cookies\JVFTMGUB.txt [ Cookie:administrator@lucidmedia.com/ ]
C:\DOCUMENTS AND SETTINGS\ADMINISTRATOR\Cookies\43B8RPXM.txt [ Cookie:administrator@onlineadtracker.co.uk/ ]
C:\DOCUMENTS AND SETTINGS\ADMINISTRATOR\Cookies\0Q20RZTO.txt [ Cookie:administrator@dc.tremormedia.com/ ]
C:\DOCUMENTS AND SETTINGS\ADMINISTRATOR\Cookies\FY6HR7Y4.txt [ Cookie:administrator@adformdsp.net/ ]
C:\DOCUMENTS AND SETTINGS\ADMINISTRATOR\Cookies\CZZQUQDQ.txt [ Cookie:administrator@server.adformdsp.net/ ]
C:\DOCUMENTS AND SETTINGS\ADMINISTRATOR\Cookies\0TJTZNJS.txt [ Cookie:administrator@atwola.com/ ]
C:\DOCUMENTS AND SETTINGS\ADMINISTRATOR\Cookies\RSGZ79JZ.txt [ Cookie:administrator@interclick.com/ ]
C:\DOCUMENTS AND SETTINGS\ADMINISTRATOR\Cookies\F49O77ID.txt [ Cookie:administrator@click.expandsearchanswers.com/ads-clicktrack/click/ ]
C:\DOCUMENTS AND SETTINGS\ADMINISTRATOR\Cookies\K7ZC2JDW.txt [ Cookie:administrator@doubleclick.net/ ]
C:\DOCUMENTS AND SETTINGS\ADMINISTRATOR\Cookies\QOYZVO3M.txt [ Cookie:administrator@adup.rotator.hadj7.adjuggler.net/ ]
C:\DOCUMENTS AND SETTINGS\ADMINISTRATOR\Cookies\HS6SS9W0.txt [ Cookie:administrator@questionmarket.com/ ]
C:\DOCUMENTS AND SETTINGS\ADMINISTRATOR\Cookies\AFEXYQQB.txt [ Cookie:administrator@serving-sys.com/ ]
C:\DOCUMENTS AND SETTINGS\ADMINISTRATOR\Cookies\FGGUJJXY.txt [ Cookie:administrator@fastclick.net/ ]
C:\DOCUMENTS AND SETTINGS\ADMINISTRATOR\Cookies\686KBOR8.txt [ Cookie:administrator@audience2media.com/servlet/ajrotator/track/pt1103192 ]
C:\DOCUMENTS AND SETTINGS\ADMINISTRATOR\Cookies\GUDBMSZI.txt [ Cookie:administrator@mediaplex.com/ ]
C:\DOCUMENTS AND SETTINGS\ADMINISTRATOR\Cookies\WCL3GY34.txt [ Cookie:administrator@advertising.com/ ]
C:\DOCUMENTS AND SETTINGS\ADMINISTRATOR\Cookies\T1JZKD4C.txt [ Cookie:administrator@collective-media.net/ ]
C:\DOCUMENTS AND SETTINGS\ADMINISTRATOR\Cookies\ATE19RRW.txt [ Cookie:administrator@ar.atwola.com/ ]
C:\DOCUMENTS AND SETTINGS\ADMINISTRATOR\Cookies\BN2T2VQY.txt [ Cookie:administrator@zedo.com/ ]
C:\DOCUMENTS AND SETTINGS\ADMINISTRATOR\Cookies\D7B8PX1L.txt [ Cookie:administrator@ad.yieldmanager.com/ ]
C:\DOCUMENTS AND SETTINGS\ADMINISTRATOR\Cookies\Y2R9FCPW.txt [ Cookie:administrator@yieldmanager.net/ ]
C:\DOCUMENTS AND SETTINGS\ADMINISTRATOR\Cookies\C7KH88QX.txt [ Cookie:administrator@liveperson.net/ ]
C:\DOCUMENTS AND SETTINGS\ADMINISTRATOR\Cookies\8WW6KRIX.txt [ Cookie:administrator@
www.burstnet.com/ ]
C:\DOCUMENTS AND SETTINGS\ADMINISTRATOR\Cookies\FZKTCT0U.txt [ Cookie:administrator@find.seekgreen.co.uk/ ]
C:\DOCUMENTS AND SETTINGS\ADMINISTRATOR\Cookies\36G8ECAS.txt [ Cookie:administrator@micklemedia.com/ ]
C:\DOCUMENTS AND SETTINGS\ADMINISTRATOR\Cookies\0NCZ6X5V.txt [ Cookie:administrator@247realmedia.com/ ]
C:\DOCUMENTS AND SETTINGS\ADMINISTRATOR\Cookies\TIGAG463.txt [ Cookie:administrator@sales.liveperson.net/ ]
C:\DOCUMENTS AND SETTINGS\ADMINISTRATOR\Cookies\WRJTMPZV.txt [ Cookie:administrator@track.adform.net/ ]
C:\DOCUMENTS AND SETTINGS\ADMINISTRATOR\Cookies\WPIIXZVH.txt [ Cookie:administrator@fidelity.rotator.hadj7.adjuggler.net/ ]
C:\DOCUMENTS AND SETTINGS\ADMINISTRATOR\Cookies\FA875G1T.txt [ Cookie:administrator@adform.net/ ]
C:\DOCUMENTS AND SETTINGS\ADMINISTRATOR\Cookies\9DZWVK00.txt [ Cookie:administrator@virginmedia.com/ ]
C:\DOCUMENTS AND SETTINGS\STEPHEN\Cookies\DBIQQ0H3.txt [ Cookie:stephen@clkads.com/adServe/banners ]
C:\DOCUMENTS AND SETTINGS\STEPHEN\Cookies\P6YBZAZF.txt [ Cookie:stephen@adsonar.com/adserving ]
2nd Scan Log
SUPERAntiSpyware Scan Log
http://www.superantispyware.comGenerated 05/01/2012 at 11:07 PM
Application Version : 5.0.1148
Core Rules Database Version : 8535
Trace Rules Database Version: 6347
Scan type : Complete Scan
Total Scan Time : 01:35:57
Operating System Information
Windows XP Home Edition 32-bit, Service Pack 3 (Build 5.01.2600)
Administrator
Memory items scanned : 504
Memory threats detected : 0
Registry items scanned : 35902
Registry threats detected : 0
File items scanned : 107745
File threats detected : 63
Adware.Tracking Cookie
cdn.complexmedianetwork.com [ C:\DOCUMENTS AND SETTINGS\ADMINISTRATOR\APPLICATION DATA\MACROMEDIA\FLASH PLAYER\#SHAREDOBJECTS\KUQSZ4L8 ]
ads1.msn.com [ C:\DOCUMENTS AND SETTINGS\DAWN\APPLICATION DATA\MACROMEDIA\FLASH PLAYER\#SHAREDOBJECTS\RXB76UBJ ]
atdmt.com [ C:\DOCUMENTS AND SETTINGS\DAWN\APPLICATION DATA\MACROMEDIA\FLASH PLAYER\#SHAREDOBJECTS\RXB76UBJ ]
img-cdn.mediaplex.com [ C:\DOCUMENTS AND SETTINGS\DAWN\APPLICATION DATA\MACROMEDIA\FLASH PLAYER\#SHAREDOBJECTS\RXB76UBJ ]
interclick.com [ C:\DOCUMENTS AND SETTINGS\DAWN\APPLICATION DATA\MACROMEDIA\FLASH PLAYER\#SHAREDOBJECTS\RXB76UBJ ]
m.uk.2mdn.net [ C:\DOCUMENTS AND SETTINGS\DAWN\APPLICATION DATA\MACROMEDIA\FLASH PLAYER\#SHAREDOBJECTS\RXB76UBJ ]
m1.2mdn.net [ C:\DOCUMENTS AND SETTINGS\DAWN\APPLICATION DATA\MACROMEDIA\FLASH PLAYER\#SHAREDOBJECTS\RXB76UBJ ]
m1.emea.2mdn.net [ C:\DOCUMENTS AND SETTINGS\DAWN\APPLICATION DATA\MACROMEDIA\FLASH PLAYER\#SHAREDOBJECTS\RXB76UBJ ]
oddcast.com [ C:\DOCUMENTS AND SETTINGS\DAWN\APPLICATION DATA\MACROMEDIA\FLASH PLAYER\#SHAREDOBJECTS\RXB76UBJ ]
serving-sys.com [ C:\DOCUMENTS AND SETTINGS\DAWN\APPLICATION DATA\MACROMEDIA\FLASH PLAYER\#SHAREDOBJECTS\RXB76UBJ ]
spe.atdmt.com [ C:\DOCUMENTS AND SETTINGS\DAWN\APPLICATION DATA\MACROMEDIA\FLASH PLAYER\#SHAREDOBJECTS\RXB76UBJ ]
2mdn.net [ C:\DOCUMENTS AND SETTINGS\STEPHEN\APPLICATION DATA\MACROMEDIA\FLASH PLAYER\#SHAREDOBJECTS\4EWY72W4 ]
ad.uk.doubleclick.net [ C:\DOCUMENTS AND SETTINGS\STEPHEN\APPLICATION DATA\MACROMEDIA\FLASH PLAYER\#SHAREDOBJECTS\4EWY72W4 ]
ads1.msn.com [ C:\DOCUMENTS AND SETTINGS\STEPHEN\APPLICATION DATA\MACROMEDIA\FLASH PLAYER\#SHAREDOBJECTS\4EWY72W4 ]
as-us.falkag.net [ C:\DOCUMENTS AND SETTINGS\STEPHEN\APPLICATION DATA\MACROMEDIA\FLASH PLAYER\#SHAREDOBJECTS\4EWY72W4 ]
atdmt.com [ C:\DOCUMENTS AND SETTINGS\STEPHEN\APPLICATION DATA\MACROMEDIA\FLASH PLAYER\#SHAREDOBJECTS\4EWY72W4 ]
b.ads1.msn.com [ C:\DOCUMENTS AND SETTINGS\STEPHEN\APPLICATION DATA\MACROMEDIA\FLASH PLAYER\#SHAREDOBJECTS\4EWY72W4 ]
broadcast.piximedia.fr [ C:\DOCUMENTS AND SETTINGS\STEPHEN\APPLICATION DATA\MACROMEDIA\FLASH PLAYER\#SHAREDOBJECTS\4EWY72W4 ]
cdn5.specificclick.net [ C:\DOCUMENTS AND SETTINGS\STEPHEN\APPLICATION DATA\MACROMEDIA\FLASH PLAYER\#SHAREDOBJECTS\4EWY72W4 ]
core.insightexpressai.com [ C:\DOCUMENTS AND SETTINGS\STEPHEN\APPLICATION DATA\MACROMEDIA\FLASH PLAYER\#SHAREDOBJECTS\4EWY72W4 ]
doubleclick.net [ C:\DOCUMENTS AND SETTINGS\STEPHEN\APPLICATION DATA\MACROMEDIA\FLASH PLAYER\#SHAREDOBJECTS\4EWY72W4 ]
ds.serving-sys.com [ C:\DOCUMENTS AND SETTINGS\STEPHEN\APPLICATION DATA\MACROMEDIA\FLASH PLAYER\#SHAREDOBJECTS\4EWY72W4 ]
ec.atdmt.com [ C:\DOCUMENTS AND SETTINGS\STEPHEN\APPLICATION DATA\MACROMEDIA\FLASH PLAYER\#SHAREDOBJECTS\4EWY72W4 ]
fr.2mdn.net [ C:\DOCUMENTS AND SETTINGS\STEPHEN\APPLICATION DATA\MACROMEDIA\FLASH PLAYER\#SHAREDOBJECTS\4EWY72W4 ]
gw.callingbanners.com [ C:\DOCUMENTS AND SETTINGS\STEPHEN\APPLICATION DATA\MACROMEDIA\FLASH PLAYER\#SHAREDOBJECTS\4EWY72W4 ]
img-cdn.mediaplex.com [ C:\DOCUMENTS AND SETTINGS\STEPHEN\APPLICATION DATA\MACROMEDIA\FLASH PLAYER\#SHAREDOBJECTS\4EWY72W4 ]
interclick.com [ C:\DOCUMENTS AND SETTINGS\STEPHEN\APPLICATION DATA\MACROMEDIA\FLASH PLAYER\#SHAREDOBJECTS\4EWY72W4 ]
kona.kontera.com [ C:\DOCUMENTS AND SETTINGS\STEPHEN\APPLICATION DATA\MACROMEDIA\FLASH PLAYER\#SHAREDOBJECTS\4EWY72W4 ]
m.uk.2mdn.net [ C:\DOCUMENTS AND SETTINGS\STEPHEN\APPLICATION DATA\MACROMEDIA\FLASH PLAYER\#SHAREDOBJECTS\4EWY72W4 ]
m1.2mdn.net [ C:\DOCUMENTS AND SETTINGS\STEPHEN\APPLICATION DATA\MACROMEDIA\FLASH PLAYER\#SHAREDOBJECTS\4EWY72W4 ]
m1.emea.2mdn.net [ C:\DOCUMENTS AND SETTINGS\STEPHEN\APPLICATION DATA\MACROMEDIA\FLASH PLAYER\#SHAREDOBJECTS\4EWY72W4 ]
media.monster.com [ C:\DOCUMENTS AND SETTINGS\STEPHEN\APPLICATION DATA\MACROMEDIA\FLASH PLAYER\#SHAREDOBJECTS\4EWY72W4 ]
media.mtvnservices.com [ C:\DOCUMENTS AND SETTINGS\STEPHEN\APPLICATION DATA\MACROMEDIA\FLASH PLAYER\#SHAREDOBJECTS\4EWY72W4 ]
media.scanscout.com [ C:\DOCUMENTS AND SETTINGS\STEPHEN\APPLICATION DATA\MACROMEDIA\FLASH PLAYER\#SHAREDOBJECTS\4EWY72W4 ]
media.tattomedia.com [ C:\DOCUMENTS AND SETTINGS\STEPHEN\APPLICATION DATA\MACROMEDIA\FLASH PLAYER\#SHAREDOBJECTS\4EWY72W4 ]
media.tiscali.co.uk [ C:\DOCUMENTS AND SETTINGS\STEPHEN\APPLICATION DATA\MACROMEDIA\FLASH PLAYER\#SHAREDOBJECTS\4EWY72W4 ]
media01.kyte.tv [ C:\DOCUMENTS AND SETTINGS\STEPHEN\APPLICATION DATA\MACROMEDIA\FLASH PLAYER\#SHAREDOBJECTS\4EWY72W4 ]
media1.break.com [ C:\DOCUMENTS AND SETTINGS\STEPHEN\APPLICATION DATA\MACROMEDIA\FLASH PLAYER\#SHAREDOBJECTS\4EWY72W4 ]
mediaplex.com [ C:\DOCUMENTS AND SETTINGS\STEPHEN\APPLICATION DATA\MACROMEDIA\FLASH PLAYER\#SHAREDOBJECTS\4EWY72W4 ]
msntest.serving-sys.com [ C:\DOCUMENTS AND SETTINGS\STEPHEN\APPLICATION DATA\MACROMEDIA\FLASH PLAYER\#SHAREDOBJECTS\4EWY72W4 ]
naiadsystems.com [ C:\DOCUMENTS AND SETTINGS\STEPHEN\APPLICATION DATA\MACROMEDIA\FLASH PLAYER\#SHAREDOBJECTS\4EWY72W4 ]
objects.tremormedia.com [ C:\DOCUMENTS AND SETTINGS\STEPHEN\APPLICATION DATA\MACROMEDIA\FLASH PLAYER\#SHAREDOBJECTS\4EWY72W4 ]
oddcast.com [ C:\DOCUMENTS AND SETTINGS\STEPHEN\APPLICATION DATA\MACROMEDIA\FLASH PLAYER\#SHAREDOBJECTS\4EWY72W4 ]
revenue.net [ C:\DOCUMENTS AND SETTINGS\STEPHEN\APPLICATION DATA\MACROMEDIA\FLASH PLAYER\#SHAREDOBJECTS\4EWY72W4 ]
s0.2mdn.net [ C:\DOCUMENTS AND SETTINGS\STEPHEN\APPLICATION DATA\MACROMEDIA\FLASH PLAYER\#SHAREDOBJECTS\4EWY72W4 ]
secure-us.imrworldwide.com [ C:\DOCUMENTS AND SETTINGS\STEPHEN\APPLICATION DATA\MACROMEDIA\FLASH PLAYER\#SHAREDOBJECTS\4EWY72W4 ]
serving-sys.com [ C:\DOCUMENTS AND SETTINGS\STEPHEN\APPLICATION DATA\MACROMEDIA\FLASH PLAYER\#SHAREDOBJECTS\4EWY72W4 ]
sftrack.searchforce.net [ C:\DOCUMENTS AND SETTINGS\STEPHEN\APPLICATION DATA\MACROMEDIA\FLASH PLAYER\#SHAREDOBJECTS\4EWY72W4 ]
spe.atdmt.com [ C:\DOCUMENTS AND SETTINGS\STEPHEN\APPLICATION DATA\MACROMEDIA\FLASH PLAYER\#SHAREDOBJECTS\4EWY72W4 ]
static.2mdn.net [ C:\DOCUMENTS AND SETTINGS\STEPHEN\APPLICATION DATA\MACROMEDIA\FLASH PLAYER\#SHAREDOBJECTS\4EWY72W4 ]
track.webgains.com [ C:\DOCUMENTS AND SETTINGS\STEPHEN\APPLICATION DATA\MACROMEDIA\FLASH PLAYER\#SHAREDOBJECTS\4EWY72W4 ]
uk.2mdn.net [ C:\DOCUMENTS AND SETTINGS\STEPHEN\APPLICATION DATA\MACROMEDIA\FLASH PLAYER\#SHAREDOBJECTS\4EWY72W4 ]
www.adsenserecipe.com [ C:\DOCUMENTS AND SETTINGS\STEPHEN\APPLICATION DATA\MACROMEDIA\FLASH PLAYER\#SHAREDOBJECTS\4EWY72W4 ]
www.virginmedia.com [ C:\DOCUMENTS AND SETTINGS\STEPHEN\APPLICATION DATA\MACROMEDIA\FLASH PLAYER\#SHAREDOBJECTS\4EWY72W4 ]
PUP.MyWebSearch
C:\PROGRAM FILES\NETSCAPE\NETSCAPE BROWSER\PLUGINS\NPMYWEBS.DLL
Trojan.Agent/Gen-Nullo[Short]
ZIP ARCHIVE( C:\QOOBOX\QUARANTINE\C\WINDOWS\SYSTEM32\_ARP_.EXE.ZIP )/ARP.EXE.1
C:\QOOBOX\QUARANTINE\C\WINDOWS\SYSTEM32\_ARP_.EXE.ZIP
ZIP ARCHIVE( C:\QOOBOX\QUARANTINE\C\WINDOWS\SYSTEM32\_SCARDSVR_.EXE.ZIP )/SCARDSVR.EXE.1
C:\QOOBOX\QUARANTINE\C\WINDOWS\SYSTEM32\_SCARDSVR_.EXE.ZIP
ZIP ARCHIVE( C:\QOOBOX\QUARANTINE\C\WINDOWS\SYSTEM32\_SETUP_.EXE.ZIP )/SETUP.EXE.1
C:\QOOBOX\QUARANTINE\C\WINDOWS\SYSTEM32\_SETUP_.EXE.ZIP
Trojan.Agent/Gen-FakeAntiSpy
C:\SYSTEM VOLUME INFORMATION\_RESTORE{A1FDC60D-0FFC-4EFA-9F97-603332CE802D}\RP787\A0070876.EXE
Trojan.Agent/Gen-FakeAlert
C:\_OTL\MOVEDFILES\04292012_043740\C_DOCUMENTS AND SETTINGS\ALL USERS\APPLICATION DATA\BWNGUKIRPGKBMLB.EXE





 button.
button. to download the ESET Smart Installer. Save it to your desktop.
to download the ESET Smart Installer. Save it to your desktop.
 button.
button.

 , and save the file to your desktop using a unique name, such as ESETScan. Include the contents of this report in your next reply.
, and save the file to your desktop using a unique name, such as ESETScan. Include the contents of this report in your next reply. button.
button.

