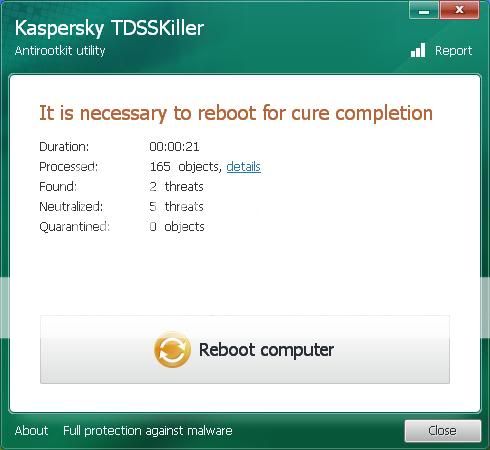
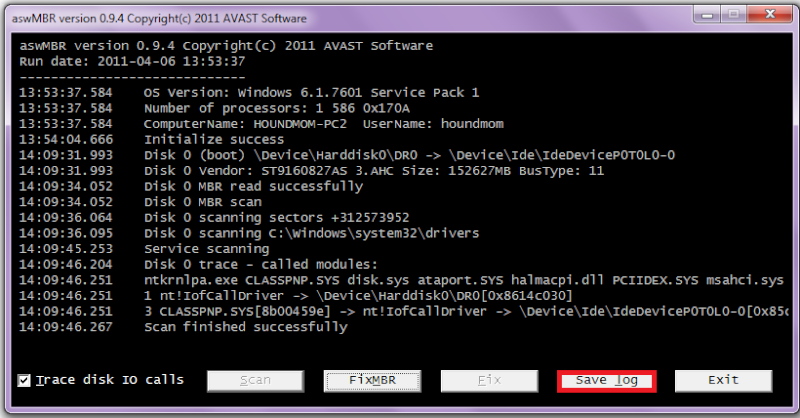
Today i was on my computer and experienced this issue, I found a few older topic on here regarding it. I ran the unhide, combo fix, and it appears to have fixed the problem the icons on my desktop have returned, i can go back on chrome etc.
Here is my log from unhide -
--------------------------------------
Unhide by Lawrence Abrams (Grinler)
http://www.bleepingcomputer.com/
Copyright 2008-2012 BleepingComputer.com
More Information about Unhide.exe can be found at this link:
http://www.bleepingcomputer.com/forums/topic405109.html
Program started at: 10/07/2012 10:41:08 PM
Windows Version: Windows Vista
Please be patient while your files are made visible again.
Processing the C:\ drive
Finished processing the C:\ drive. 332322 files processed.
Restoring the Start Menu.
* 505 Shortcuts and Desktop items were restored.
Searching for Windows Registry changes made by FakeHDD rogues.
- Checking HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\Explorer
- Checking HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\System
* DisableTaskMgr policy was found and deleted!
- Checking HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\ActiveDesktop
* HidNoChangingWallPaperden policy was found and deleted!
- Checking HKCU\Software\Microsoft\Windows\CurrentVersion\Explorer\Advanced
* Start_ShowControlPanel was set to 0! It was set back to 1!
* Start_ShowHelp was set to 0! It was set back to 1!
* Start_ShowMyComputer was set to 0! It was set back to 1!
* Start_ShowMyDocs was set to 0! It was set back to 1!
* Start_ShowMyMusic was set to 0! It was set back to 1!
* Start_ShowMyPics was set to 0! It was set back to 1!
* Start_ShowPrinters was set to 0! It was set back to 1!
* Start_ShowRun was set to 0! It was set back to 1!
* Start_ShowSearch was set to 0! It was set back to 1!
* Start_ShowSetProgramAccessAndDefaults was set to 0! It was set back to 1!
* Start_ShowRecentDocs was set to 0! It was set back to 2!
* Start_ShowNetConn was set to 0! It was set back to 1!
* Start_ShowNetPlaces was set to 0! It was set back to 1!
* Start_TrackDocs was set to 0! It was set back to 1!
* Start_TrackProgs was set to 0! It was set back to 1!
* Start_ShowUser was set to 0! It was set back to 1!
* Start_ShowMyGames was set to 0! It was set back to 1!
Restarting Explorer.exe in order to apply changes.
Program finished at: 10/07/2012 10:48:20 PM
Execution time: 0 hours(s), 7 minute(s), and 11 seconds(s)
-------------------------------------
ANd here is my log from the Malwarebytes Anti Malware -
--------------------------
Malwarebytes Anti-Malware (Trial) 1.65.0.1400
www.malwarebytes.org
Database version: v2012.10.07.04
Windows Vista Service Pack 1 x86 NTFS (Safe Mode/Networking)
Internet Explorer 8.0.6001.19088
lalit :: LALITMAMTA-PC [administrator]
Protection: Disabled
08-10-2012 08:19:07
mbam-log-2012-10-08 (08-19-07).txt
Scan type: Full scan (C:\|)
Scan options enabled: Memory | Startup | Registry | File System | Heuristics/Extra | Heuristics/Shuriken | PUP | PUM
Scan options disabled: P2P
Objects scanned: 514337
Time elapsed: 1 hour(s), 35 minute(s), 9 second(s)
Memory Processes Detected: 0
(No malicious items detected)
Memory Modules Detected: 0
(No malicious items detected)
Registry Keys Detected: 0
(No malicious items detected)
Registry Values Detected: 2
HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run|nqJmDLLyhpVVQC.exe (Trojan.FakeAlert) -> Data: C:\ProgramData\nqJmDLLyhpVVQC.exe -> Quarantined and deleted successfully.
HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Run|UJPTuOBg9fQk3U (Trojan.FakeAlert) -> Data: C:\ProgramData\UJPTuOBg9fQk3U.exe -> Quarantined and deleted successfully.
Registry Data Items Detected: 2
HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Advanced|Start_ShowMyComputer (PUM.Hijack.StartMenu) -> Bad: (0) Good: (1) -> Quarantined and repaired successfully.
HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Advanced|Start_ShowSearch (PUM.Hijack.StartMenu) -> Bad: (0) Good: (1) -> Quarantined and repaired successfully.
Folders Detected: 0
(No malicious items detected)
Files Detected: 4
C:\ProgramData\NQJMDLLYHPVVQC.EXE (Trojan.FakeAlert) -> Quarantined and deleted successfully.
C:\ProgramData\UJPTUOBG9FQK3U.EXE (Trojan.FakeAlert) -> Quarantined and deleted successfully.
C:\Lalit\USB\Lalit\New Folder\pwdremover.exe (PSWTool.PdfCracker) -> Quarantined and deleted successfully.
C:\ProgramData\ajrO5zbYAPBR2R.exe (Trojan.FakeAlert) -> Quarantined and deleted successfully.
(end)
-------
Here is my log from unhide -
--------------------------------------
Unhide by Lawrence Abrams (Grinler)
http://www.bleepingcomputer.com/
Copyright 2008-2012 BleepingComputer.com
More Information about Unhide.exe can be found at this link:
http://www.bleepingcomputer.com/forums/topic405109.html
Program started at: 10/07/2012 10:41:08 PM
Windows Version: Windows Vista
Please be patient while your files are made visible again.
Processing the C:\ drive
Finished processing the C:\ drive. 332322 files processed.
Restoring the Start Menu.
* 505 Shortcuts and Desktop items were restored.
Searching for Windows Registry changes made by FakeHDD rogues.
- Checking HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\Explorer
- Checking HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\System
* DisableTaskMgr policy was found and deleted!
- Checking HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\ActiveDesktop
* HidNoChangingWallPaperden policy was found and deleted!
- Checking HKCU\Software\Microsoft\Windows\CurrentVersion\Explorer\Advanced
* Start_ShowControlPanel was set to 0! It was set back to 1!
* Start_ShowHelp was set to 0! It was set back to 1!
* Start_ShowMyComputer was set to 0! It was set back to 1!
* Start_ShowMyDocs was set to 0! It was set back to 1!
* Start_ShowMyMusic was set to 0! It was set back to 1!
* Start_ShowMyPics was set to 0! It was set back to 1!
* Start_ShowPrinters was set to 0! It was set back to 1!
* Start_ShowRun was set to 0! It was set back to 1!
* Start_ShowSearch was set to 0! It was set back to 1!
* Start_ShowSetProgramAccessAndDefaults was set to 0! It was set back to 1!
* Start_ShowRecentDocs was set to 0! It was set back to 2!
* Start_ShowNetConn was set to 0! It was set back to 1!
* Start_ShowNetPlaces was set to 0! It was set back to 1!
* Start_TrackDocs was set to 0! It was set back to 1!
* Start_TrackProgs was set to 0! It was set back to 1!
* Start_ShowUser was set to 0! It was set back to 1!
* Start_ShowMyGames was set to 0! It was set back to 1!
Restarting Explorer.exe in order to apply changes.
Program finished at: 10/07/2012 10:48:20 PM
Execution time: 0 hours(s), 7 minute(s), and 11 seconds(s)
-------------------------------------
ANd here is my log from the Malwarebytes Anti Malware -
--------------------------
Malwarebytes Anti-Malware (Trial) 1.65.0.1400
www.malwarebytes.org
Database version: v2012.10.07.04
Windows Vista Service Pack 1 x86 NTFS (Safe Mode/Networking)
Internet Explorer 8.0.6001.19088
lalit :: LALITMAMTA-PC [administrator]
Protection: Disabled
08-10-2012 08:19:07
mbam-log-2012-10-08 (08-19-07).txt
Scan type: Full scan (C:\|)
Scan options enabled: Memory | Startup | Registry | File System | Heuristics/Extra | Heuristics/Shuriken | PUP | PUM
Scan options disabled: P2P
Objects scanned: 514337
Time elapsed: 1 hour(s), 35 minute(s), 9 second(s)
Memory Processes Detected: 0
(No malicious items detected)
Memory Modules Detected: 0
(No malicious items detected)
Registry Keys Detected: 0
(No malicious items detected)
Registry Values Detected: 2
HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run|nqJmDLLyhpVVQC.exe (Trojan.FakeAlert) -> Data: C:\ProgramData\nqJmDLLyhpVVQC.exe -> Quarantined and deleted successfully.
HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Run|UJPTuOBg9fQk3U (Trojan.FakeAlert) -> Data: C:\ProgramData\UJPTuOBg9fQk3U.exe -> Quarantined and deleted successfully.
Registry Data Items Detected: 2
HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Advanced|Start_ShowMyComputer (PUM.Hijack.StartMenu) -> Bad: (0) Good: (1) -> Quarantined and repaired successfully.
HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Advanced|Start_ShowSearch (PUM.Hijack.StartMenu) -> Bad: (0) Good: (1) -> Quarantined and repaired successfully.
Folders Detected: 0
(No malicious items detected)
Files Detected: 4
C:\ProgramData\NQJMDLLYHPVVQC.EXE (Trojan.FakeAlert) -> Quarantined and deleted successfully.
C:\ProgramData\UJPTUOBG9FQK3U.EXE (Trojan.FakeAlert) -> Quarantined and deleted successfully.
C:\Lalit\USB\Lalit\New Folder\pwdremover.exe (PSWTool.PdfCracker) -> Quarantined and deleted successfully.
C:\ProgramData\ajrO5zbYAPBR2R.exe (Trojan.FakeAlert) -> Quarantined and deleted successfully.
(end)
-------


 by sUBs
by sUBs